Key2XS bridges the gap between identity management and physical key infrastructure — delivering compliance, audit readiness, and operational control.
Three pillars that define how Key2XS extends IAM governance to the physical world
Every physical key tied to a verified digital identity through your IAM system.
Access policies defined once, enforced everywhere — across all connected key systems.
Every key issuance, return, and access event logged with full user attribution.
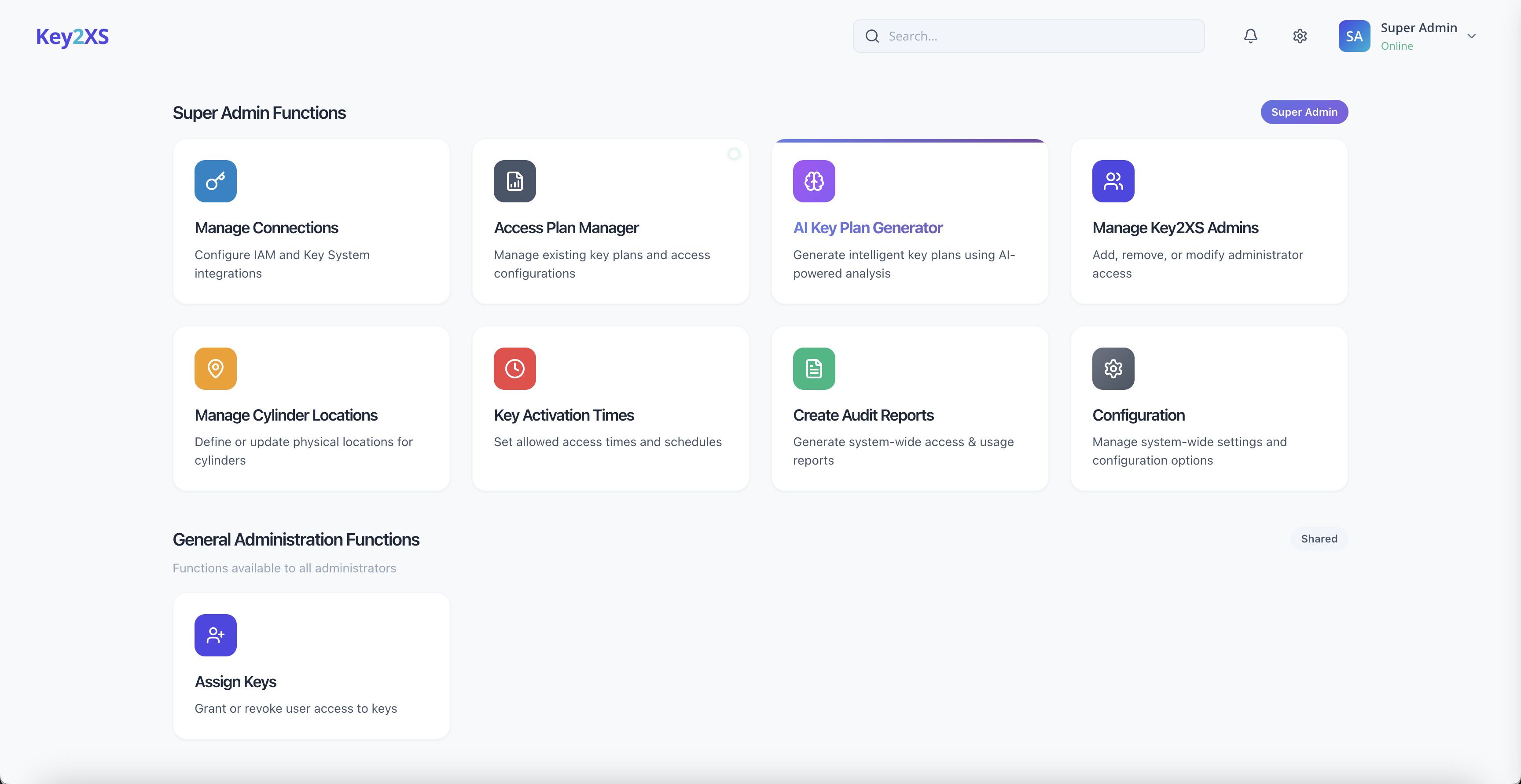
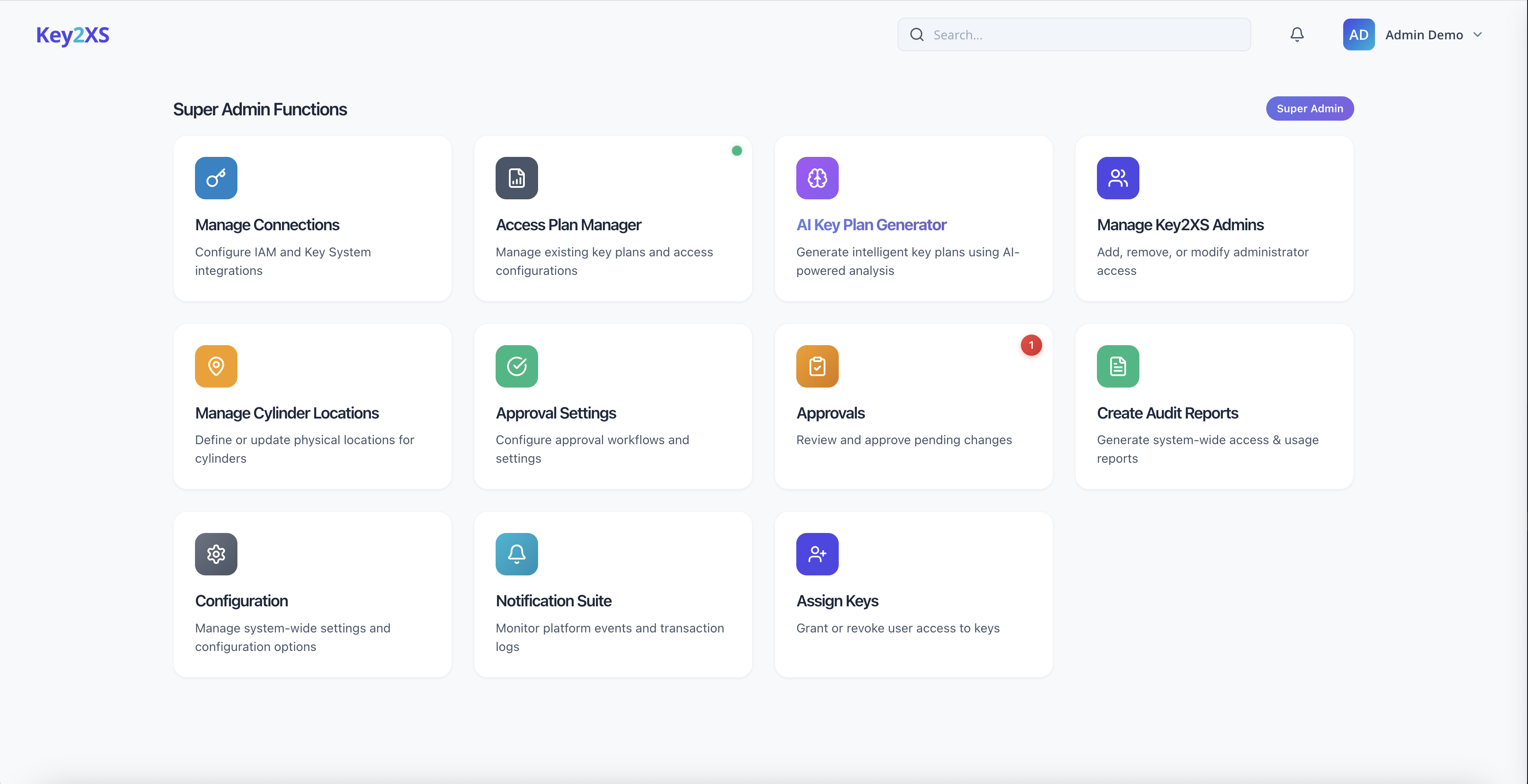
32 features across 6 categories — everything you need for physical access governance
Role-based or user-based approvers, scoped per operation type and key plan.
Rules stay pending until approved — nothing syncs unreviewed to key systems.
Built-in report generator for EU regulatory compliance evidence.
Every insert, update, and delete tracked with full user attribution.
Custom filters by user, key, cylinder, event type, and date range with export.
Configurable email alerts triggered by platform events.
Okta, Entra ID, SailPoint, One Identity, OpenText, and more out of the box.
Joiner/Mover/Leaver events trigger automatic access changes via webhooks, polling, or SCIM.
Standards-compliant inbound provisioning from any SCIM-capable IAM system.
Automatic and manual attribute mapping between IAM and access profiles.
Single sign-on with IAM of choice and callback handling for seamless authentication.
Create, assign, return, and archive keys with full status tracking.
Organize cylinders into groups and link them to locations.
Geographic visualization of cylinder locations on interactive maps.
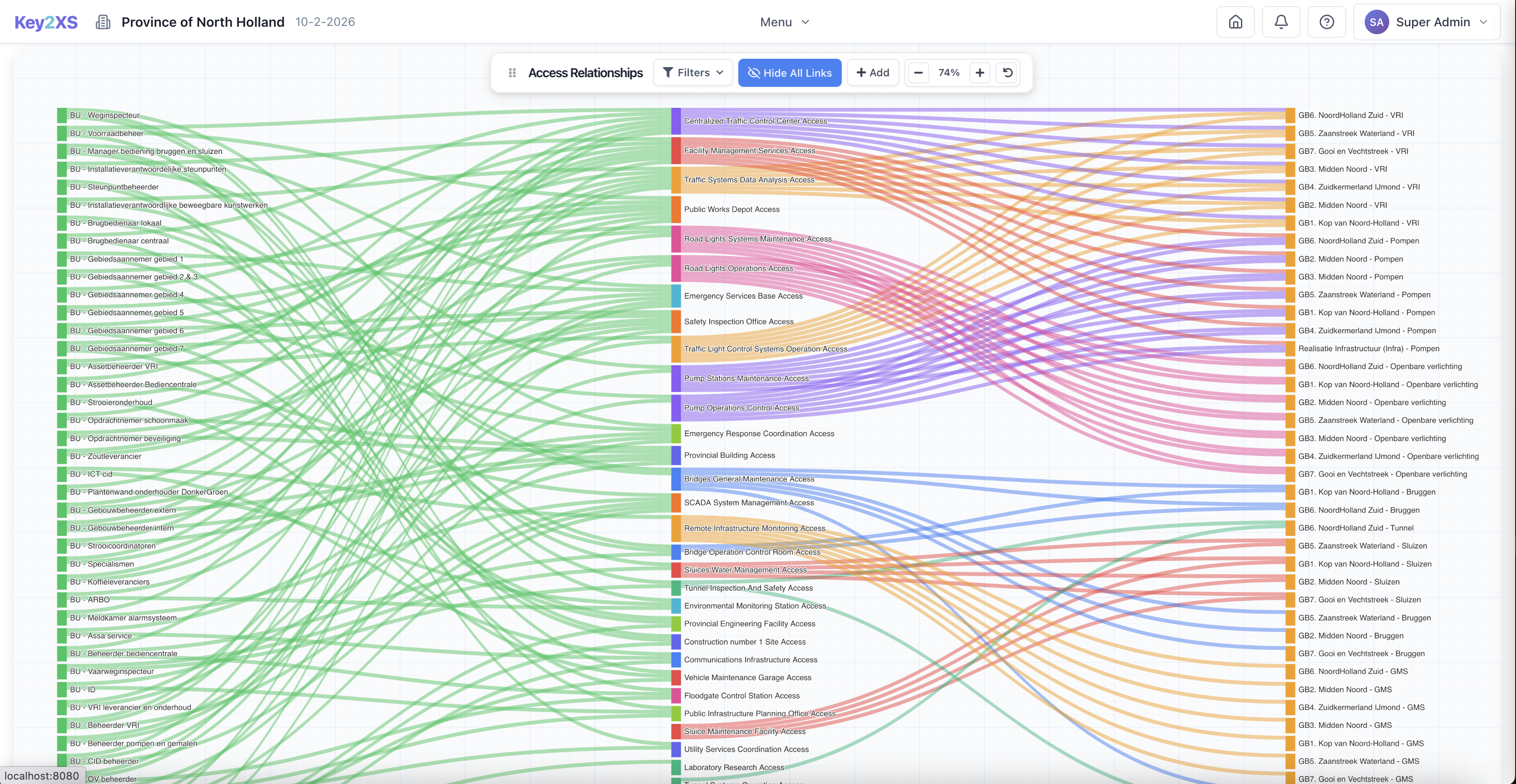
Define access rules by role, department, or job function.
Configure which rules sync to which physical key systems with status monitoring.
Provision Bluetooth mobile keys directly from the platform.
5-stage pipeline from CSV discovery to access profile generation with human review.
AI adapts to your industry, governance model, language, and cultural context.
AI recommends cylinder assignments based on organizational patterns.
User counts, access stats, and active rule trends over configurable time periods.
Interactive visualization of role-to-cylinder access mappings.
Automatic token expiration and refresh for secure session management.
Super-admin, sub-admin, and user roles with fine-grained route guards.
Every granted and denied event tracked per user, key, and cylinder.
Proactive alerts for expiring integration credentials before they cause failures.
Detailed failure reasons: network errors, missing keys, configuration issues.
Manage all IAM, key system, and external connections from one interface.
Step-by-step setup flows for every integration type.
GIS and mapping data for location-based asset management.
Bulk import organizational data for AI key plan processing.
Manage external employees and contractors without an IAM system.
A unified interface for identity-linked physical access management

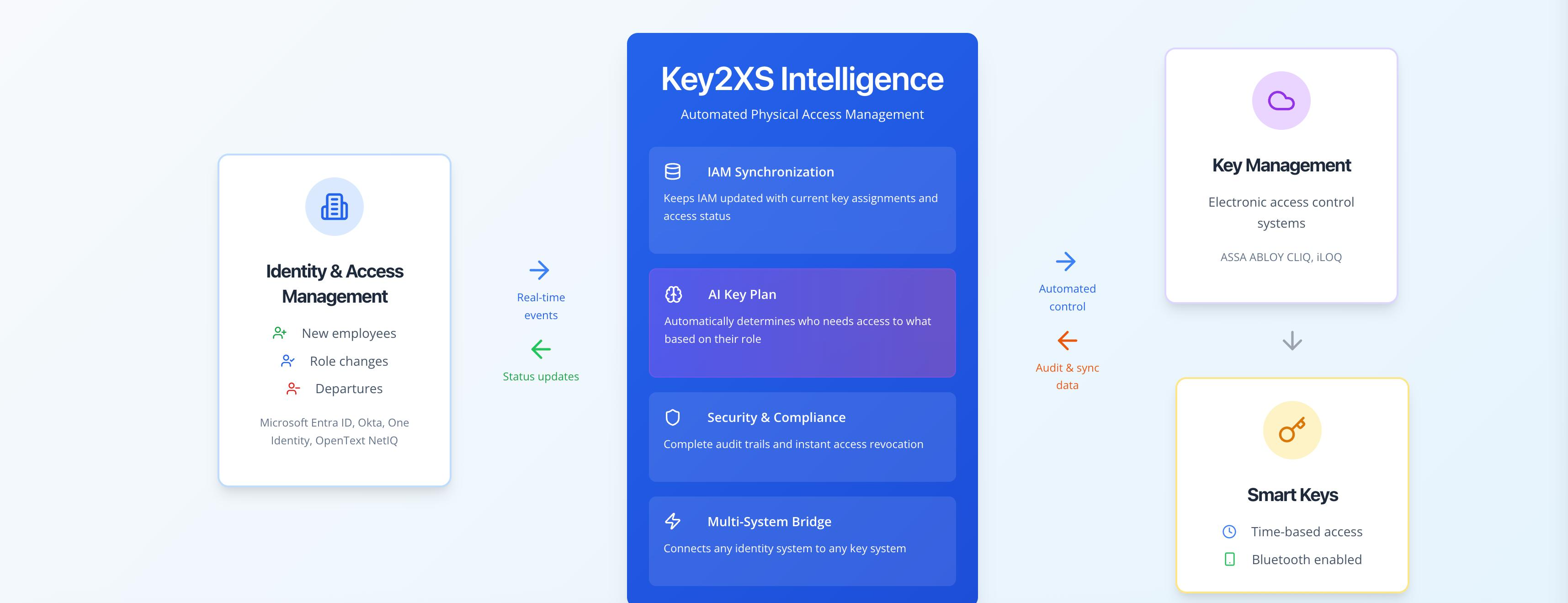
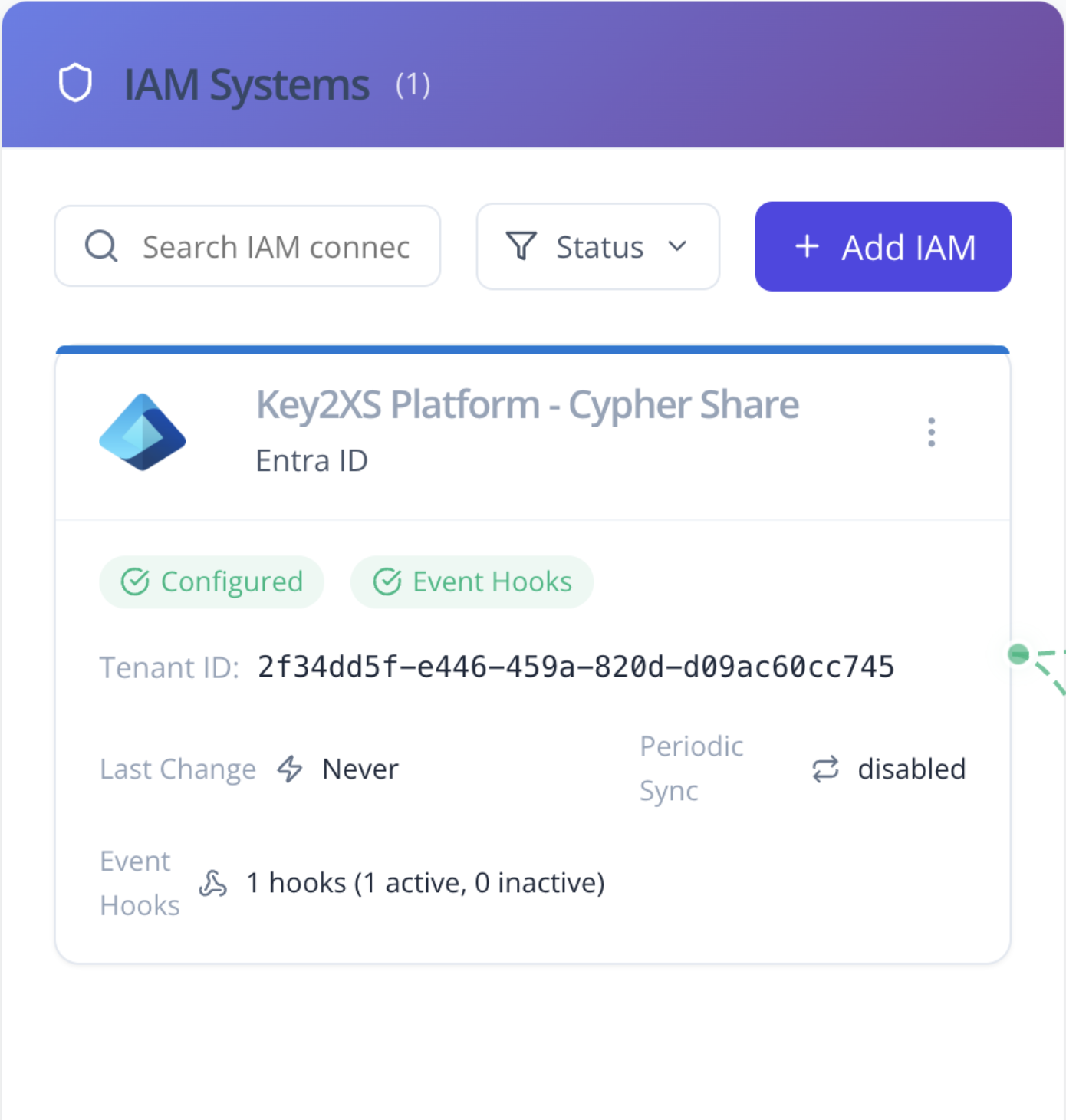
Connects to your existing IAM providers and physical key systems




-svg.png)
From first conversation to full deployment — a structured path to securing your physical access infrastructure
Understand your key infrastructure, IAM environment, and compliance requirements
Map your current key systems, cylinders, and identity sources. Define integration scope for your IAM platform and key system.
Deploy Key2XS on a subset of your infrastructure. Connect to your IAM system and key management platform. Validate audit trail and compliance reporting.
Expand to all sites, keys, and cylinders. Train security and facilities teams. Go-live with full governance and compliance monitoring.
Dedicated account management, platform updates and new integrations, compliance support for CER/NIS2 audits.
Choose the model that fits your organization's security and infrastructure requirements
Fully managed cloud deployment. No infrastructure to maintain — automatic updates and built-in redundancy.
Deploy within your own data center. Full control over your environment for strict data residency requirements.
Combine cloud management with on-premises data processing. Balance operational flexibility with data sovereignty.
Discover how Key2XS extends IAM governance to physical access.