Get control of your physical access.
One platform linking identity to physical keys — governance, compliance and audit readiness for critical organizations.
From Physical Blind Spots to Digital Governance.
Zero Visibility
No real-time insight into who holds access to critical areas.
Audit Fatigue
Proving compliance takes days of manual reconstruction, not minutes.
No Accountability
When incidents occur, manual logs fail to provide an audit trail.
Policy Drift
Physical access privileges rarely match your current security policies.
Key2XS Bridging the Physical-Digital Divide.
Policy
Enforcing access through policy and approval flows
Identity
Linking physical keys to digital identities
Traceability
Complete audit trails for every physical access event
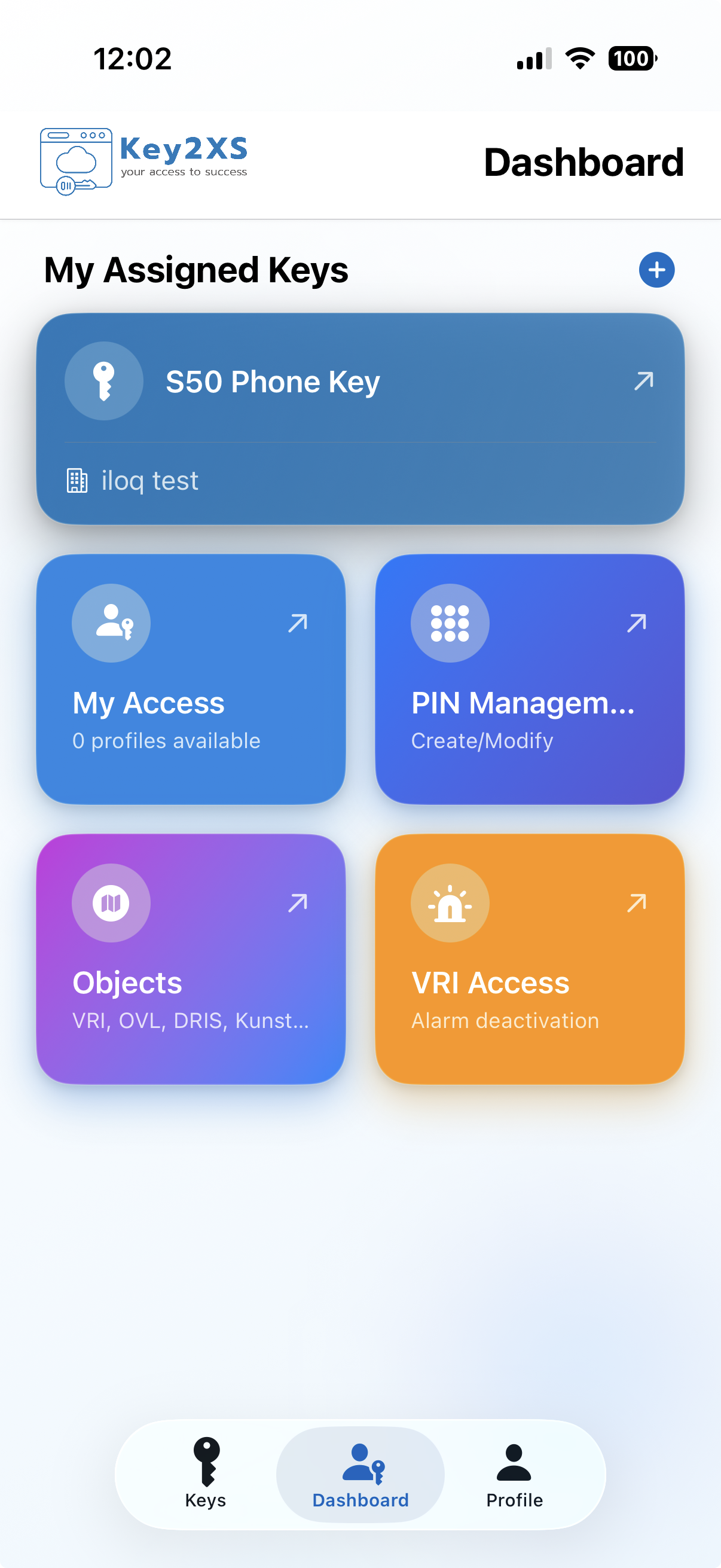
How Key2XS governs physical access
From identity and policy to physical keys and audit evidence — in one controlled flow.
Identity & Access Management
- Joiner
- Mover
- Leaver
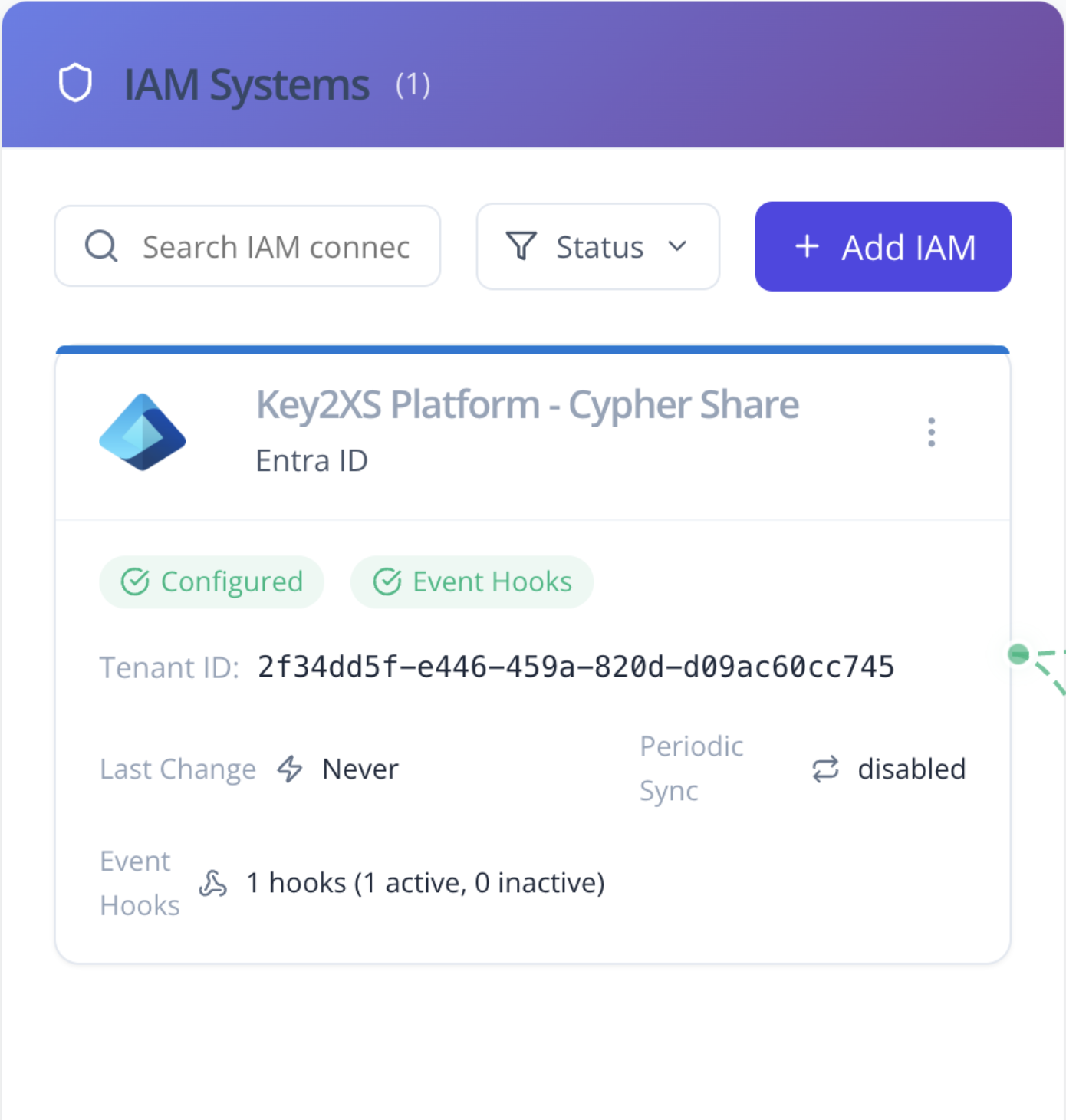
SailPoint ISC, Microsoft Entra ID, Okta, One Identity, OpenText NetIQ/ILM
Key2XS Intelligence
Automated Physical Access Management
IAM Synchronization
Keeps IAM updated with current key assignments and access status
AI Key Plan
Automatically determines who needs access to what based on their role
Security & Compliance
Complete audit trails and instant access revocation
Multi-System Bridge
Connects any identity system to any key system
Key Management
Electronic access control systems
iLOQ, ASSA ABLOY (eCLIQ, PROTEC² CLIQ, ABLOY PULSE)
Smart Keys
Designed for critical organisations.
Key2XS is used in environments where physical access impacts public safety, service continuity or regulatory compliance. Typical organisations include:
Utility Sector
Key2XS provides comprehensive access governance solutions for the Utility Sector. Our platform ensures security, compliance, and operational efficiency.
Industrial Sector
Key2XS provides comprehensive access governance solutions for the Industrial Sector. Our platform ensures security, compliance, and operational efficiency.
Transport Sector
Key2XS provides comprehensive access governance solutions for the Transport Sector. Our platform ensures security, compliance, and operational efficiency.
Healthcare Sector
Key2XS provides comprehensive access governance solutions for the Healthcare Sector. Our platform ensures security, compliance, and operational efficiency.
EU Directive Implementation Tracker
The EU's Critical Entities Resilience (CER) Directive requires all member states to strengthen the resilience of critical infrastructure. We track implementation progress in real time, so you always know where each country stands and what it means for your compliance obligations.
Serving organisations where physical access directly impacts safety, continuity and compliance.
See how this works in practiceFrom governed access to measurable impact.
How structured access governance directly translates into compliance, efficiency and risk reduction.
Governance drivers
Our metrics
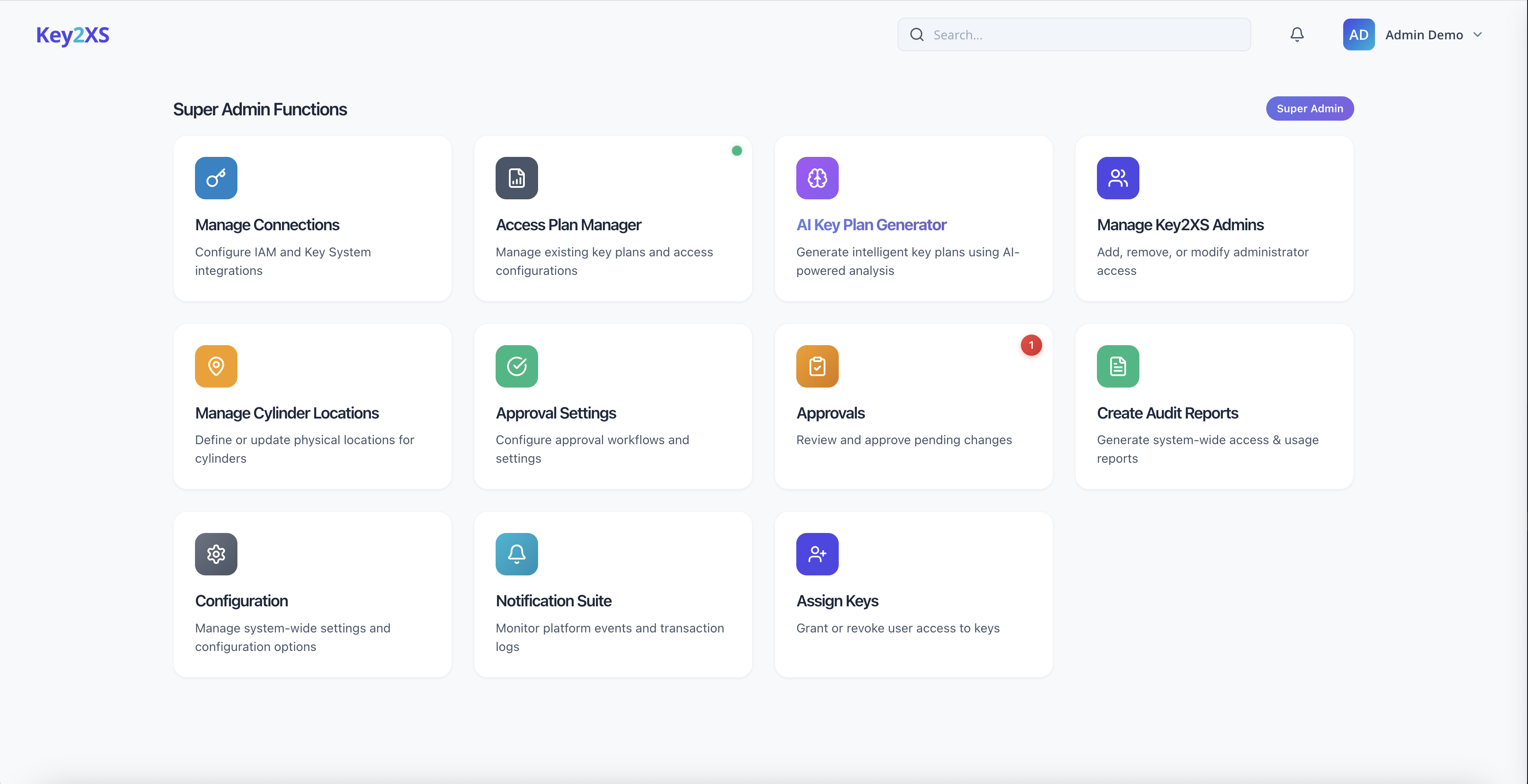
Why Key2XS was built
We were looking for a single solution for key management - It didn't exist yet
Traditional key systems and IAM solutions operated as isolated islands. Key2XS unites these worlds into one integrated platform.
Discover our solution →
Co-Founder Key2XS

Co-Founder Key2XS

Co-Founder Key2XS

Co-Founder Key2XS

Smart key systems are IT. Treat them that way.
Read more
CER compliance calendar for newly appointed critical entities
Read more
CER implementation across the EU. Status as of 8 February 2026
Read more
How the Key2XS Mobile App Creates a Seamless Operational Layer Across CLIQ, iLOQ and the Key2XS Platform
Read more
SoftBank’s third-party data breach: what happened, what was exposed, and how Key2XS would have changed the story
Read more Live Now
Live Now
One Identity UNITE User and Partner Conference Vienna
One Identity UNITE is where customers, partners, prospects and industry experts from across the globe meet to discuss solutions, innovations and challenges in the identity security market. The event will be held in person in Vienna, 2-6 March, 2026.
Trade Mission to RSA Conference San Francisco
CyberSec Europe
CyberSec Netherlands 2026
See Key2XS in action
What will be included in your guided walkthrough;
- Identity-linked access control
- Policy-driven approvals
- Real-time access visibility
- Audit-ready evidence
Get started with Key2XS today
Get a guided walkthrough of how identity, policy and physical access come together in one auditable system.
FAQ
Everything you need to know before getting started — from integrations and security to compliance and deployment.
Key2XS is designed for critical organisations where physical access directly impacts safety, continuity and compliance. This includes government institutions, utilities, industrial facilities, transport organisations, and healthcare providers.
During a demo, we'll walk you through the Key2XS platform, show you how it integrates with your existing systems, and discuss your specific access management challenges. The demo typically takes 30-45 minutes.
No, Key2XS is designed to work alongside your existing access control and key management systems. We integrate with your current infrastructure rather than replacing it.
Key2XS integrates with major IAM systems, key management solutions, and access control platforms including ASSA ABLOY (eCLIQ, PROTEC² CLIQ, CLIQ Remote, ABLOY PULSE via CLIQ Web Manager), iLOQ, Microsoft Entra ID, and various other identity providers.
.webp)







-svg.png)




