The Overlap Between NIS2 and CER: What Critical Entities Need to Know
In the evolving landscape of European cybersecurity and infrastructure protection, two major regulations stand out: the NIS2 Directive (Network and Information Security) and the CER Directive (Critical Entities Resilience). While they originate from different policy domains — cybersecurity versus infrastructure resilience — they are closely interlinked in both intent and impact.
Understanding their overlap is essential for critical entities aiming to stay compliant, avoid duplication, and build a unified resilience strategy.
Shared Objectives
Both NIS2 and CER aim to strengthen the resilience of entities that provide essential services across the EU, such as:
-
Energy
-
Water
-
Transport
-
Digital infrastructure
-
Health
-
Public administration
Key shared goals include:
-
Preventing and mitigating the impact of disruptions, whether digital (cyberattacks) or physical (sabotage, natural disasters),
-
Promoting risk-based approaches to security,
-
Ensuring incident reporting and response readiness,
-
Encouraging a coordinated European approach to critical infrastructure protection.
Key Differences
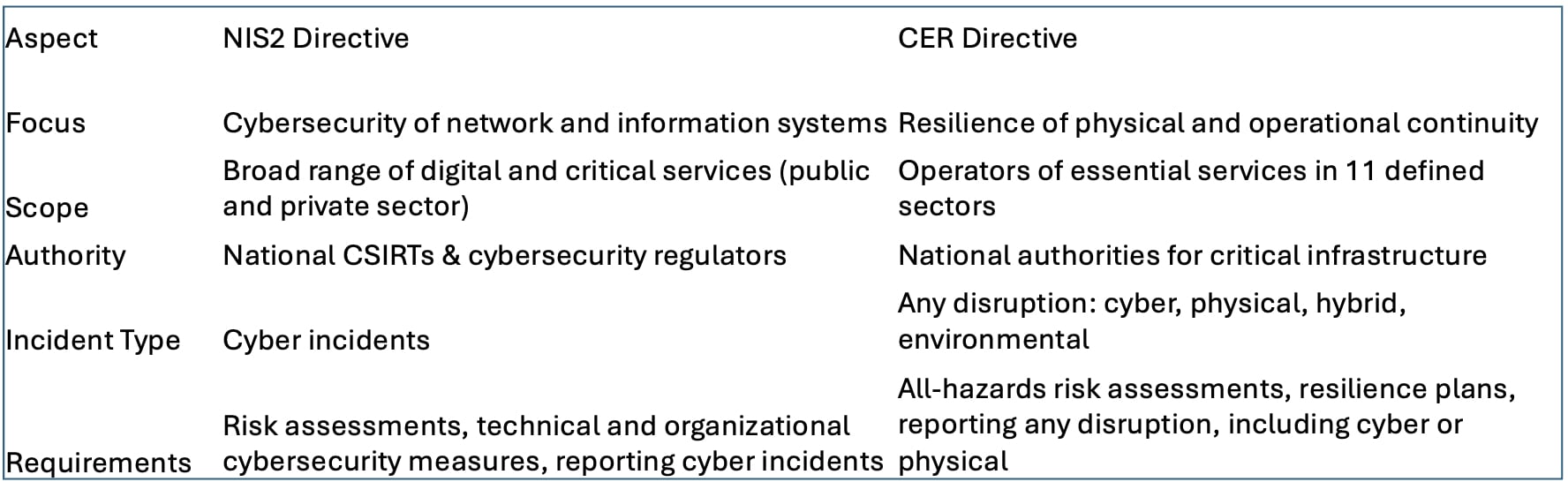
Despite these differences, NIS2 and CER converge in several operational areas.
Points of Convergence
1. Risk Management and Governance
Both directives require a structured approach to risk management:
-
Under NIS2, this includes cybersecurity controls like access management, encryption, and patching.
-
Under CER, entities must assess risks to operational continuity, including supply chain dependencies, natural hazards, and malicious attacks.
Unified approach: Organizations should adopt an integrated risk framework that accounts for both digital and physical threats.
2. Incident Reporting
Both directives enforce mandatory incident reporting:
-
NIS2: Notify the competent authority/CSIRT within 24 hours after a cyber incident.
-
CER: Report any significant disruption (including physical sabotage, natural disasters, or third-party failure) as soon as possible.
Unified approach: Implement centralized incident response procedures and ensure legal, cybersecurity, and operations teams are aligned on what qualifies as reportable.
3. Supply Chain Security
Both frameworks recognize third-party risk as a key vulnerability:
-
NIS2 demands measures for managing digital supply chain risk (e.g. software providers, MSPs).
-
CER emphasizes supplier dependencies for physical infrastructure and operations.
Unified approach: Use vendor risk assessments, contracts with security clauses, and access management systems (such as IAM and electronic key management) to manage supplier access.
4. Resilience Planning
-
NIS2 entities must ensure the availability, integrity, authenticity and confidentiality of systems.
-
CER requires a formal resilience plan covering contingency, continuity, and recovery in case of disruptions.
Unified approach: Integrate business continuity planning (BCP) and disaster recovery (DR) into both cybersecurity and physical operations, with regular testing and audits.
Strategic Alignment Tips
-
Appoint a single accountable function (CISO, CRO, or Resilience Officer) to coordinate NIS2 and CER efforts.
-
Centralize asset, access, and risk data in a shared platform.
-
Invest in tools that bridge cybersecurity and physical security, such as:
-
IAM platforms (e.g. Microsoft Entra, SailPoint),
-
Smart key systems (e.g. ASSA ABLOY CLIQ or iLOQ),
-
Logging and auditing solutions (e.g. Key2XS).
Conclusion
The NIS2 and CER directives are two sides of the same coin: resilient, secure, and protected critical infrastructure. By understanding their overlap and aligning efforts, organizations can reduce complexity, avoid duplicated effort, and strengthen their defenses against both digital and physical threats.
About Key2XS
Key2XS helps critical entities unify their physical and digital access strategies by integrating CLIQ smart keys into IAM platforms like Entra ID and SailPoint. Our platform supports full compliance with NIS2 and CER, providing automated provisioning, incident logging, and real-time auditing across your infrastructure and supply chain.
Learn more on how Key2XS can help your organization to become CER & NIS2 compliant at https://key2xs.com/whitepaper-nis2-cer